Aclaimant's Journey to SOC2 by Aclaimant CTO Joel Friedman
By Joel Friedman
Jan 09, 2020
These days, system security is as important as functionality, if not more, when it comes to purchasing SaaS products. Many of us are starting to understand this as consumers, however we do not necessarily realize the importance of system security when it comes to software we use everyday at work. At Aclaimant, we go above and beyond to show our customers that security is not an afterthought but rather a core to our business. Most recently we have done this by obtaining out SOC 2 Type II certification.
WHAT IS SOC 2
SOC 2 is a framework of five key “trust principles” designed by the American Institute of Certified Public Accountants (AICPA) for service providers to ensure protection of sensitive and private information is well managed. Today, these trust principles are applicable to most SaaS companies. This framework was designed by the AICPA as a bar to which organizations should hold themselves to in order to convey the importance of security. The SOC 2 certification has become the standard enterprise SaaS companies can use to validate the services they provide are secure and trustworthy.
This graphic shows the five key principles and some of the main points of each.
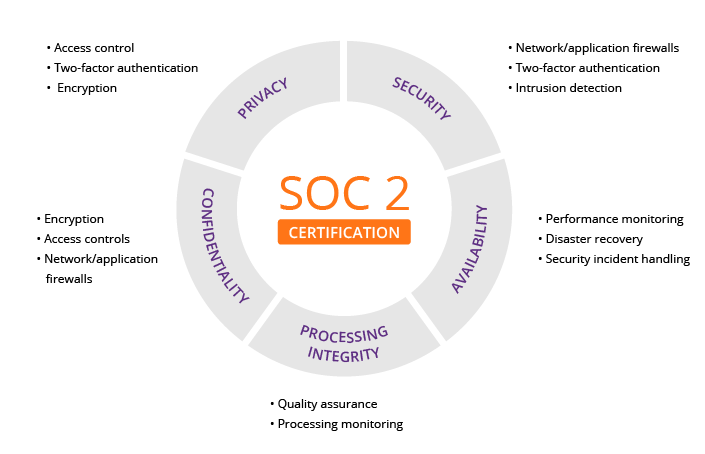
Source: https://www.imperva.com/learn/data-security/soc-2-compliance/
WHY WE STARTED OUR SOC 2 JOURNEY WHEN WE DID
At Aclaimant, we have always taken security seriously. As the CTO and acting CISO, the security of Aclaimant is one of my main areas of focus. My career has taken me to different companies where security was top priority. Most notably was my time spent at a trading firm, where one can only imagine the importance of security. This mentality has become core to how I think about building systems, and was one of the founding principles since the early days of Aclaimant.
During late 2016s and early 2017s, our sales pipeline began to include larger businesses and enterprises. While this was great for our company by increasing our average contract size, it also increased the number of requests we had for security questionnaires and assessments. These all took a significant amount of time to complete. Previously, we had written up our own security Q&A to be shared with prospects in order to minimize additional questions, but this no longer was the case.
Enterprise security teams look for SOC 2
Large enterprises look for standards-based proof that companies take security seriously, and one of the most common is the SOC 2 report.
Habits are easier to build than to change
It is imperative that everyone at the company follows the processes and controls that auditors look for. It is always easier to ensure these are foundational to employees as a company grows as opposed to attempting to change the habits of employees to conform to these controls.
Reduces risk
The processes that are necessary to complete a SOC 2 audit are not just for show. The controls increase the security across the entire company.
THE PATH WE TOOK
To get started, we took a look at several key areas over the course of three months. While it is common for a company to spend six to 12 months preparing for their first SOC 2 audit, we opted for a more accelerated approach. In order for this pace to work there were two thing we had to start with: A solid understanding of the certification process, and eagerly looking for help in the form of information and, more importantly, tools to aid in the process.
UNDERSTANDING THE CERTIFICATION PROCESS
-
Read lots of articles and blog posts
-
Find others within your network that have gone through the process and ask them for their insights
-
If you’re going through the SOC 2 process, feel free to reach out to us
-
-
Interview auditors
-
During the interview process, they all provide a great overview of the process involved
-
Additionally, you will probably find a good audit firm in the process
-
POLICIES
A major portion of the audit assures that your policies are complete and comprehensive. Additionally, the auditors check that your organization follows that guidelines set out in your policies. I found the following to be useful when working through our policies.
Don’t start from scratch
"If I have seen further than others, it is by standing on the shoulders of giants.”
- Isaac Newton
-
Policies templates can be found on several sources online
-
Find a tool to help generate your policies based on recommendations and the needs of your company
All employees must read and sign all policies
-
Point out the key takeaways for each role since there will be a lot of information within the policies. Our full policy packet is 59 pages long
Review policies annually
-
Certification requires policies are reviewed annually
-
Things change over time and you want to ensure your policies keep up-to-date with these changes
UNDERSTAND ON-BOARDING AND OFF-BOARDING
Use SSO
-
SSO simplifies the on-boarding process. For a lot of software, new users do not need to be invited when using SSO
-
During off-boarding, it becomes much easier to lock terminated employee out of systems using SSO
-
Ensures only employees with company email are using the tool
Build checklists
-
Ensure you know which tools employees are using, even if they are added during the employee’s tenure
-
When an employee leaves, use the checklist to lock down and remove access to all tools within 24 hours of termination
KEEP TRACK OF VENDORS
-
Know which vendors your company is using and how they use your data
-
Becomes important in other compliance undertakings, including GDPR, CCPA, etc.
-
-
Perform assessments on these vendors
-
Ensure your vendors are as careful with the data you provide them as your organization is with the data
-
Your customers will not be able to trust you if you share the data with an untrustworthy vendor
-
-
When off-boarding a vendor, ensure you understand their data deletion policy and can speak to it in the future
USE TOOLS TO HELP
During our process, we found several tools that assisted with various parts of the process. These tools helped not only in understanding how to better and faster put controls in place, but also helped monitor many of the controls. Here are some of the most beneficial ones.
-
-
SSO
-
-
-
Controls monitoring
-
Policy generation and employee sign-off
-
Employee background checks
-
Vendor management
-
-
-
Database and server access restriction
-
Audit logs of access and actions
-
-
-
On-boarding and off-boarding checklists
-
Vendor and employee access tracking
-
-
-
Password management
-
COMPLETING THE AUDIT
Most of the work was around collecting the supporting documentation. Supporting documentation is the data used to indicate to the auditors that we had implemented and followed the necessary controls.
Examples of controls we provided supporting documentation
-
Following the necessary off-boarding for any employee terminated within the timeframe of our audit
-
New features added to the product followed the software development lifecycle
-
Including pull requests and testing prior to release
-
-
Monitoring your cloud infrastructure
-
Logs stored for a significant amount of time
-
Patches updated on cloud machines
-
-
Databases backed up on a schedule
-
Background checks performed on new employees
Because of the several tools we used, as well as the continuous controls monitoring, the process took about two weeks to complete, and we were even able to perform it remotely (we are a remote-first company, after all ).
ANNOUNCING OUR SOC2 CERTIFICATION
We are excited to announce that we were able to pass our SOC 2 Type II auditor on our first try with a clean opinion. We could not have done it without our learnings from others and from the tools we choose to use. If you or your company are looking to go through the SOC 2 process and looking for some guidance please reach out to us at soc2@guidance.aclaimant.com



Comments